| |
| Exposing the Password Secrets of Paltalk |
|
|
|
|
|
|
|
| |
| |
|
| |
| |
|
Paltalk
is one of the emerging instant messenger with more than 4 million
members around the world. It features thousands of chat rooms, video
conferencing, PC to Phone calls etc.
|
|
| It is a universal messenger which supports simultaneous conversation
using leading messengers such as GTalk, AIM, MSN, ICQ, Yahoo & Facebook
etc. |
| |
| |
|
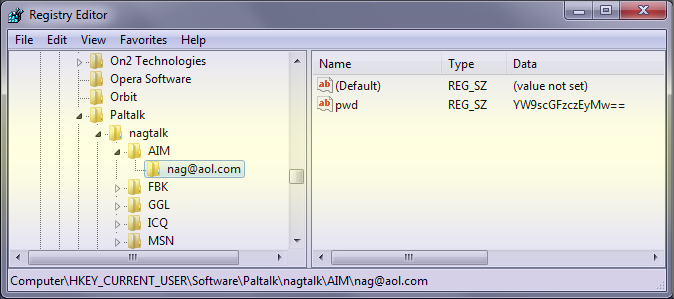
Like most of IM clients,
Paltalk also stores the user account details including
passwords in the registry for subsequent logins so that user do not
have to enter the password every time. Note that the password is
stored only if user has selected 'Save Password' at login time.
Paltalk saves main Paltalk account password in the Registry
at following location under the sub key named after your nickname
(login name)
|
|
|
HKEY_CURRENT_USER\Software\Paltalk\<nick_name> |
|
|
|
Actual encrypted password is stored under above key with value name
as 'pwd'.
For example, in my case the encrypted password for my
nickname ('nagtalk') is stored at following location as shown in the
above screen shot. |
|
|
HKEY_CURRENT_USER\Software\Paltalk\nagtalk |
|
| In addition to main Paltalk account password, it also stores
individual messenger (such as Yahoo, Gtalk, MSN etc) passwords under
unique keyname for each messenger. For example, AIM messenger account
information is stored under following registry key (refer to above
screenshot) |
|
| HKEY_CURRENT_USER\Software\Paltalk\nagtalk\AIM |
|
| Now all the AIM account passwords are stored under this location
with the key name as login name of the respective account. For example,
my AIM account login (nag@aol.com) is stored under following registry
key (refer to above screenshot) |
|
| HKEY_CURRENT_USER\Software\Paltalk\nagtalk\AIM\nag@aol.com |
|
| The password for each messenger account is encoded with BASE64 algorithm
and stored in the registry value named 'pwd' under the respective
account key. |
| |
| |
|
Paltalk uses its own
proprietary algorithm to encrypt the main account password which is
stored in the registry. In my case, the encrypted password text
looks like this, "2890297528213388275533842923294822881697". From
this encrypted text we can get the length of original password by
dividing it by 4. This leads to the fact that each group of the four
characters in encrypted password refers to single character in
original password.
All other messenger (such as Gtalk,
Yahoo, MSN etc) passwords are encoded with simple BASE64 algorithm
and can easily decoded to get the original password.
|
| |
| |
|
Here are the detailed steps for
decrypting the encrypted Paltalk account password.
|
|
|
| Here you need to first find the Paltalk installation drive letter.
Install location is generally present at following registry location |
|
|
HKEY_CURRENT_USER\Software\Paltalk |
|
Under this key, there is a registry value named 'InstallerAppDir'
which contains complete installed path of Paltalk. We just need the
drive letter from this path.
Once you get the drive letter, you
can use GetVolumeInformation function as show below to get the serial
number for this drive. |
|
DWORD dwSerial;
DWORD dwSize = 256;
char strSerial[256];
if( GetVolumeInformation(strDrive, 0, 0, &dwSerial, 0,0,0,0) == TRUE
)
{
sprintf_s(strSerial, dwSize, "%08X", dwSerial);
}
|
| Finally we will get 8 character serial number which is later used in
actual decryption process. |
| |
| |
|
Next we perform union of Paltalk nickname
(login name) and drive serial number by coupling one character from
nickname & serial number alternatively. For example, in my case it will
appear like below
|
| |
Nickname: nagtalk
Drive
serial no: 12345678
Union text: n1a2g3t4a5l6k78 |
| |
| Next we will form a bigger string by combining
this union string multiple times until it is double the length of the
original password. Note that we can get the length of original password
by dividing encrypted password by 4. For example, if the original
password length is 15 then we need to combine above string 2 times
leading to final union string as shown below. |
|
Final Union Text:
n1a2g3t4a5l6k78n1a2g3t4a5l6k78
|
|
|
|
In each step of the decryption operation, we
take 4 characters from encrypted password. But only first 3 characters
are actually used here, the 4th character is ignored. Each time, one
character from 'Final union string' is taken and subjected to some magic
operations. Finally its added to the integer form of 3 characters taken
from encrypted text. The concrete algorithm for each step of decryption
operation is shown below.
|
|
dwUnionLen = strlen('n1a2g3t4a5l6k78');
strEnc3Char = 3 chars from encrypted text
strFinalUnion =
n1a2g3t4a5l6k78n1a2g3t4a5l6k78
p = atol(strEnc3Char);
b = strFinalUnion[dwUnionLen+i-1];
d = 0x86 - b;
d = d - i;
OrgPassChar = p + d; |
|
| In each step of the above decryption operation, variable
'OrgPassChar' contains each character from original password. This loop
is to be repeated N number of times where N refers to the length of
original password. |
| |
| |
|

|
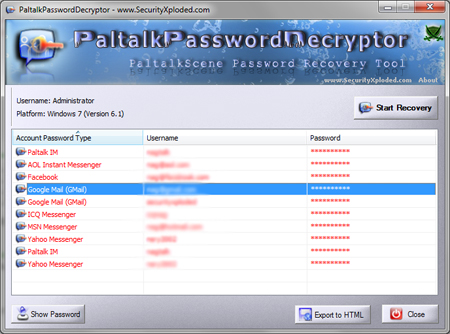
PaltalkPasswordDecryptor is a dedicated tool to recover passwords
stored by Paltalk. It can instantly recover main Paltalk
password as well as other messenger passwords for all accounts stored
by Paltalk.
|
|
|
|
|
| PaltalkPasswordDecryptor is a portable tool which does not require
installation and work across wide range of platforms starting from
Windows XP to Windows 7. You can also use our other tool,
IMPasswordDecryptor
to recover the Paltalk passwords along with other instant messenger
passwords. |
| |
| |
|
Above article explains in detail how Paltalk stores the account
password using its own proprietary encryption algorithm and shows how
one can manually decrypt such password to recover the original
password.
Note that above decryption process is based on latest
version of Paltalk Messenger (Version 9.9 build 367) and it may
change with upcoming versions of the Messenger. |
| |
| |
|
|
|
| |
| |
| |
| |